9 Most Common Ways Of Maintaining Your Online Anonymity
 |
| Most Common Ways Of Maintaining Your Online Anonymity |
What Occurs If Your Internet Privacy Is Violated
Your vulnerability to cyberattacks arises from the ease with which hackers may follow your online activities when you have no internet privacy. If you don't put in place the necessary security measures, you run the danger of:
Data breaches: When hackers gain access to your email, passwords, or personal information, there is a data breach. The dark web may be used to sell or misuse this information, putting users at risk of financial loss, phishing scams, and other security issues.
Identity theft: Online privacy concerns facilitate hackers' access to personal information, which they can use to steal or impersonate you. Your Social Security number could be used by them to open fraudulent accounts, obtain access to your bank accounts, and carry out crimes under your identity.
Browser cookies: Websites may install tracker cookies on your computer to track your online activities if privacy settings are not followed. Websites may utilize this data to bombard you with adverts or cause your computer to lag. These cookies could be intercepted by hackers, who would then take what they need to steal your identity or ruin your money.
Surveillance: A technique known as "camfecting" allows hackers to gain access to your camera. Malware known as "camfecting" gives them remote access to your computer. Increasing privacy helps stop hackers from monitoring and intruding.
Data exploitation: Without your permission, businesses frequently gather and examine user data. Market research, targeted advertising, and other uses are possible for this data.
Compromised messaging: Private messages, including as emails and texts, are susceptible to being viewed by unauthorized individuals in the absence of secure messaging software. Confidentiality violations or harm to your relationships in both your personal and professional life could arise from this.
Can One Be Wholly Anonymous on the Internet?For the typical person, it is nearly hard to stay completely anonymous on the internet. Many obstacles must be overcome in order to achieve this level of anonymity, including the potential need to spend a lot of money on technologies that can mask your IP address, turn off activity records from your internet service provider (ISP), remove your digital footprint, and more. Even while total anonymity might be difficult to achieve, you can improve your online privacy by making use of useful tools like VPNs, encrypted search engines, and encryption. |
How Do I Browse Online Without Being Monitored?Utilizing a private search engine, turning on a privacy-focused browser, or putting a VPN into practice are the three greatest ways to browse without being monitored. To keep oneself safe from internet trackers, you can use any one of these three effective strategies. |
Most Common Ways Of Maintaining Your Online Anonymity
 |
1. Disable browser cookies
Websites use little files called cookies to track your online activity, which compromises your privacy. Disabling cookies can help you stay more anonymous online. You may instantly disable cookies in popular browsers like Google Chrome, Mozilla Firefox, and Safari by making changes to the settings. By doing this, you prevent websites from collecting and tracking your data, which lowers the likelihood of online espionage.
For instance, to disable cookies in Google Chrome:
Launch Chrome
In the upper right corner, click the three vertical dots (kebab menu).
When you click Settings, a new window will appear.
Select the Security and Privacy tab.
Select the tab for third-party cookies.
Set "Block third-party cookies" to ON.
Alternatively, you can use your browser's incognito mode or enable a "do not track signal" under privacy and security to conceal your online activities. Websites will be unable to track your data as a result, but your IP address will still be recorded.
The distinction between privacy and anonymityOnline privacy entails managing the information you disclose, avoiding unsolicited observation, and guarding against the breach of your private data. It usually indicates that you wish to avoid drawing attention from the public. On the other hand, internet anonymity is what you wish to use to go public yet keep your true identity hidden. Activists, journalists, whistleblowers, and artists who would rather remain anonymous typically make this choice (usually because of safety concerns). It should be sufficient to abide by a few fundamental internet privacy guidelines if you wish to safeguard your data and shield yourself from unauthorized surveillance. If so, read our comprehensive blog post explaining what digital privacy is and how to protect it in your day-to-day activities. However, we shall soon outline the primary actions to perform if your actual objective is to completely conceal your identity. But isn't it possible to completely remove your digital imprint by only using your web browser's incognito (private browsing) mode? You can, but it won't exactly turn you into an Internet wizard. This is the explanation. |
2. Make use of a blocker for ads
Ad-blocking browser add-ons hide tracking cookies and scripts and block intrusive advertisements. You can stop these websites from tracking your online activities by blocking these adverts. An appropriate ad blocker ought to work with all browsers, including Chrome, Firefox, and Safari.
In order to prevent hackers from accessing your computer or gathering personal data without your permission, it should successfully block pop-up advertisements and other features. Verify whether your search browser has an integrated ad-block addon to increase your online privacy. You can download and install one if not.
3. Use the email and app encryption messaging illustration to learn about the encryption technologies for email and messaging
The built-in encryption features of Gmail, Mailvelope, and WhatsApp prevent unwanted users from hacking messages. Some platforms require third-party encryption services that are compatible with your device or operating system. When using compatible devices, many encryption services are free to use.
4. Safeguard your wireless networks
 |
| Turn on Wifi All Day You May Lost All Money |
To protect your online privacy and stop data invasions, or unwanted access to your network, you must secure your Wi-Fi. Hackers can quickly figure out weak passwords, such as your hometown or name. Make sure you use WPA3 encryption, the most recent Wi-Fi security upgrade, and generate a strong password for your Wi-Fi connection. By taking these precautions, you will hide your online activity and be shielded from any potential threats.
It's not as hard as you would believe to create a strong password. To make sure your passwords are safe from hackers, use these suggestions:
Use a combination of symbols, numbers, and letters.
Make sure your sentences are at least 11 characters long.
Steer clear of your name and typical phrases.
Make use of password strength checkers.
A strong password example might be ILov3P@ndaS3cur3ity55!
5. Steer clear of public WiFi when using sensitive data
Public Wi-Fi networks are usually available at cafes, airports, and hotels; however, they are not adequately secured to protect your online activities. Looking at private login credentials or sensitive online banking information in public puts your information at danger and makes it simple for hackers to obtain access. It's advisable to stay away from utilizing unprotected public Wi-Fi for important tasks without a secure VPN connection.
Although using public Wi-Fi networks can be dangerous, there are several circumstances in which doing so is acceptable. If you read news articles or browse frequently and are only accessing non-sensitive information, then using a public Wi-Fi network is usually acceptable. Use a secured browser for any login-required activity, such as social media browsing. It's crucial to exercise caution, though, and refrain from sending or viewing critical information via these networks.
6. Maintain updating your software
Updates for your software are necessary to protect your data. Frequently, the most recent upgrades come with security patches, performance enhancements, and bug fixes. These updates fix holes that hackers might use to access your device or data without authorization.
Windows and Apple usually provide automatic upgrades once a month. Turn on automatic updates from the device's settings tab to reduce the possibility of security lapses and preserve an encrypted online space.
7. Take care before posting anything online
 |
These days, social media is all around us. All people have accounts on Facebook, Twitter, Instagram, and TikTok, but you should be mindful of the information these platforms potentially disclose about you. In addition to monitoring your private data and using it for customized marketing, the content you provide online might divulge a great deal about your personal life.
A lot of the time, your social media page includes details about you, such your name, occupation, education, and residence. This entire list of details could be utilized to follow you.
Consider the overall impression that your post gives about you. Even while a single post might not seem very personal, your entire body of work can reveal a lot about you. Information you provide can give insight into your temperament and general demeanor. This information can be used by scammers and hackers to attack you. Employers may utilize this information to choose whether to recruit you (or retain you on staff).
| • Posting images or names of your family members should be avoided • Think carefully about what you include in the images that you share. They might have personal information about you, such your license plate number, or they might have identifiable landmarks that indicate where you live. |
8. Forget logging into your Google account
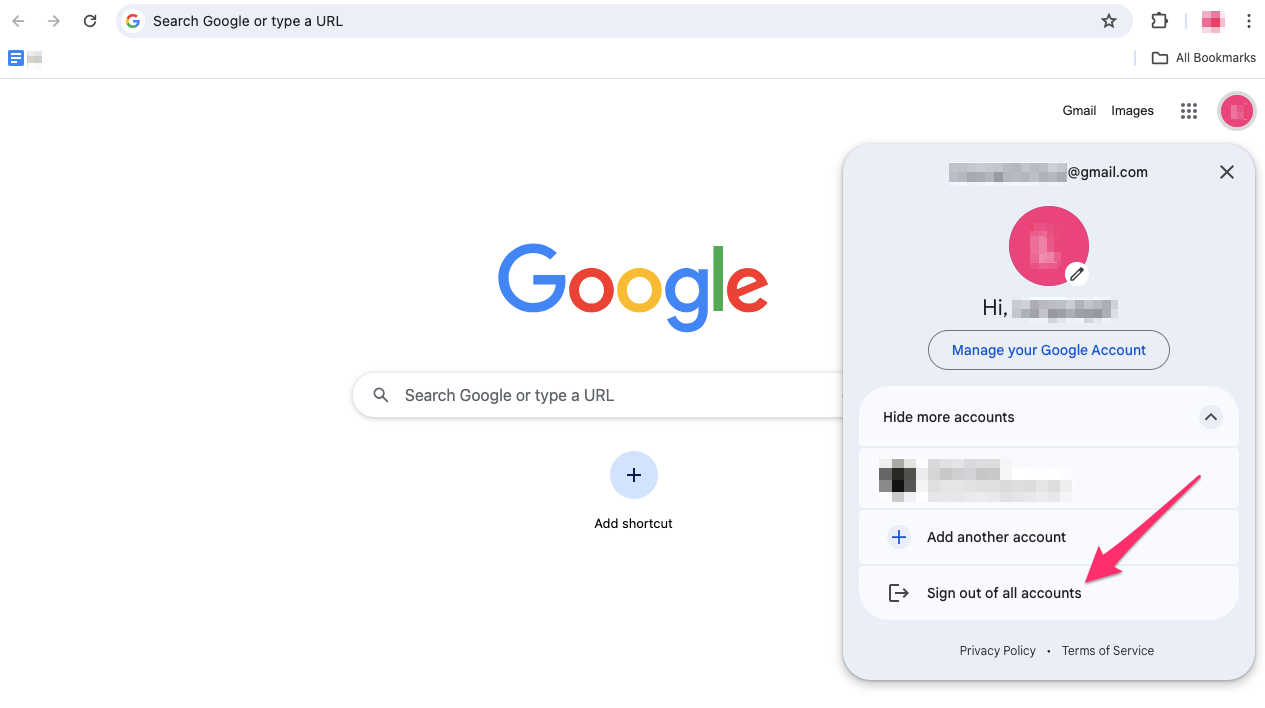 |
Google, primarily for advertising, gathers and keeps a ton of consumer data—a fact not hidden. Once you log into your Google account, you reveal several confidential information including the following:
Your exact Geolocation
Your habits and way of browsing
Your search record on websites collaborating with Google
Your interactions— likes, comments, and more—showcase
Logging out of your Google account—and staying logged off when at all possible—is the least you can do to hide your data.
9. Not use a smartphone (if at all possible)
Have you ever felt as though your phone is surreptitiously monitoring you? Although they might not be as tangible, mobile gadgets really carry many security and privacy risks. Many applications would not function as expected without access to your location, microphone, contacts, and other data. True privacy disasters abound from Google Maps and Uber Eats to basic weather and fitness applications.
Since it's quite tough to stop them from monitoring you at all levels, ideally you should avoid using such gadgets at all. If you cannot live without a smartphone, however, think about acquiring as private and safe mobile device as best alternative. Generally speaking, iOS is more secured than Android. If you want anonymity, though, you should have a gadget with more sophisticated features, including Purism Librem 5, Blackphone PRIVY 2.0, or Bittium Tough Mobile 2C. Visit our site to see the whole list of the top privacy-oriented phones.
In summary
It's almost impossible to be really anonymous online. You can, however, take precautions to safeguard your privacy and make tracking you more difficult. Examine the privacy settings of the websites, apps, and social media networks that you utilize.
 10 Best Free Online Chat Sites that You Are Anonymously with Strangers 10 Best Free Online Chat Sites that You Are Anonymously with Strangers These top 10 best anonymous chat rooms are where you can meet new people, find friends and talk with people all over the world for ... |
 Best Ways To Watch Youtube Anonymously Best Ways To Watch Youtube Anonymously How to browse Youtube anonymously? You can use third-party apps or turn on Incognito Mode with easy steps |
 Top 13 Anonymous Social Networking Apps 2024/2025 Top 13 Anonymous Social Networking Apps 2024/2025 Here are several social networking apps that let you communicate with others and express your ideas and feelings without worrying about having your identity revealed, ... |